Coronavirus-related phishing attacks and business email compromise (BEC) scams skyrocketed 3,000% from mid-March through early June, according to mid-year analysis from the Agari Cyber-Intelligence Division (ACID).
As chronicled in our H2 2020 Email Fraud & Identity Deception Trends Report, the year began with expectations of record-breaking profits for email threat groups—long before most of us had ever even heard of SARS-CoV-2.
For one thing, successful email scams have been growing far less dependent on technological know-how than on skillful social engineering. For another, our researchers were the first to document the fact that Nigerian email fraudsters who have pioneered BEC methodologies now face competition from sophisticated Eastern European crime syndicates looking for a piece of the action.
Then along came COVID-19. Suddenly, tens of millions of corporate employees were working from home, their security, access, and accounting controls in a state of flux, if not outright improvisation. Needless to say, the pandemic provided the perfect pretext for swindlers bent on exploiting a period of unprecedented uncertainty.
To understand the dynamics in play, here are three key findings that made the last six months so consequential.
Phishing Surge: Two-Thirds of Email-based Identity Deception Scams Pose as Brands
In mid-March, email attacks leveraging the coronavirus outbreak erupted with the number of imposters posing as the World Health Organization (WHO), the Centers for Disease Control (CDC) and other healthcare-related brands jumping light years beyond levels seen in early February.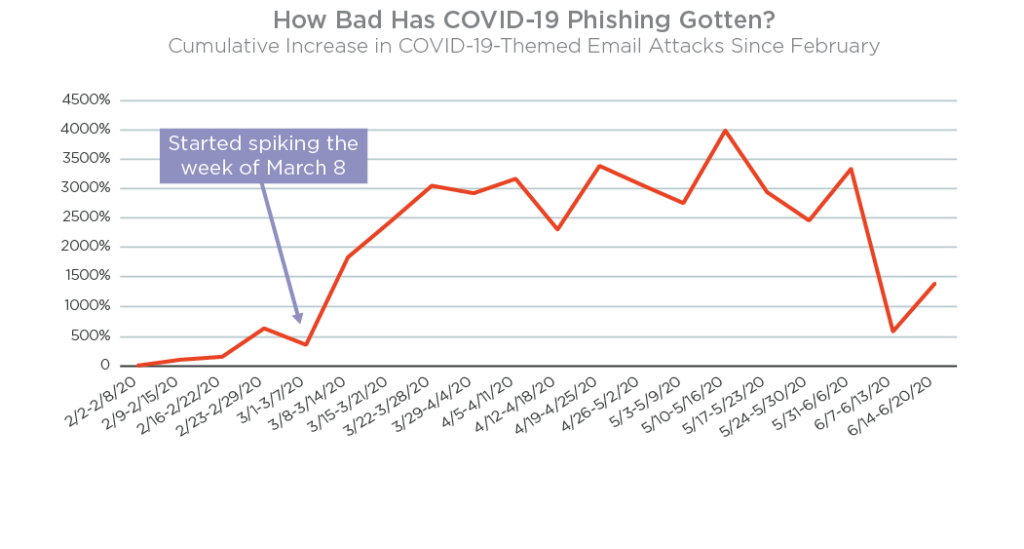
It's not at all surprising. Scam artists have always sought to profit when crisis strikes and fears are running high. Check out the correlation between phishing attacks and Google search interest related to COVID-19.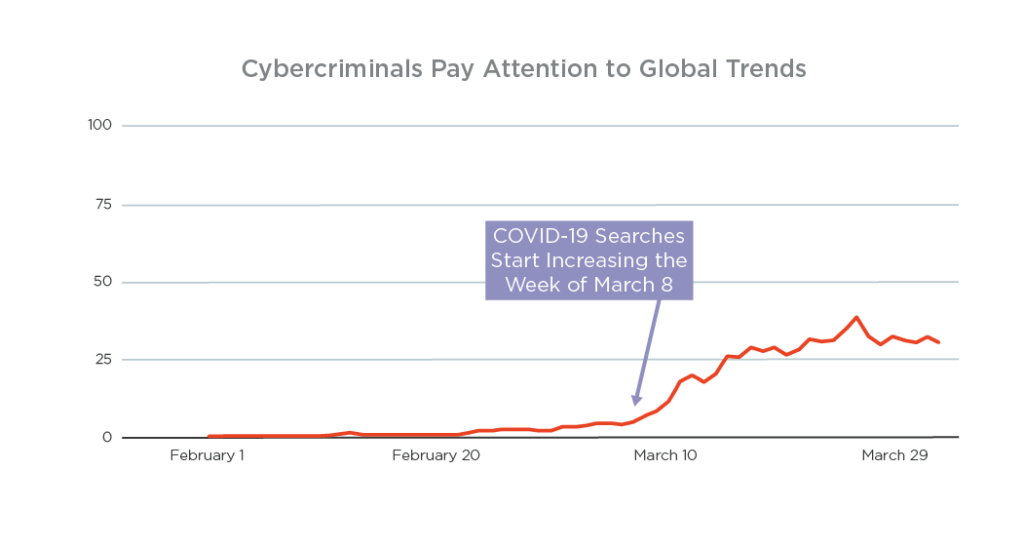
In addition to grappling with remote working, housebound children, financial distractions, and health anxieties, corporate users of Microsoft Teams and Office 365 in particular found themselves bombarded by a never-ending stream of credentials harvesting campaigns from attackers posing as the CDC and others.
The attackers' objective in such strikes: account takeovers (ATOs) of company email accounts and web applications, giving infiltrators the freedom to gather intel, steal data and IP, and plant ransomware undetected.
BEC: Impersonating Trusted Individuals Takes New Twists, Pays Big
As the weeks wore on, these larger-scale attacks gave way to brazen new forms of BEC.
The fraud group we've dubbed Ancient Tortoise, for instance, has used COVID-19 as the pretext for changes to payment details when targeting companies in aging financial reports scams by posing as members of a supplier's accounts receivables team and demanding payment for overdue invoices.
Meanwhile, the first-reported BEC group operating out of Russia—an outfit we call Cosmic Lynx—has been using the coronavirus to build rapport with its intended victims in multimillion dollar mergers-and-acquisition ruses that involve using domain spoofing and savvy social engineering in dual impersonations of both a targeted company's CEO and outside legal counsel.
Fresh Riffs, Same Costly Song
Despite all this, COVID-themed cons began to trail off by mid-June, replaced by the familiar rhythm of BEC. Though that's not to say things returned to whatever use to pass as "normal."
Today, 70% of BEC emails are sent from free webmail accounts, up sharply from 54% at the end 2019 as attackers put a premium on speed and flexibility with these temporary, disposable assets.
Meanwhile, gift cards continue to be the preferred form of payment in BEC ploys—thanks to being easily sold in online cryptocurrency exchanges. But the gap in revenues generated through high-volume, low-yield gift card rackets and precision-targeted wire transfer schemes continues to widen.
During the first half of 2020, the amount requested in gift card average averaged $1,348, compared to nearly $1,600 at the end of 2019.
At the same time, amounts sought in wire transfer schemes now average $66,790, up from $55,395 in just 180 days. The maximum requested in a wire transfer crimes observed by ACID so far this year: $1,555,770—more than double the $680,456 sought in the fourth quarter 2019.
As troubling as these last six months have been, they may pale in comparison to what comes next.
Second-Half Outlook: ATO Outbreak Ahead?
Even as the specific feints used by phishing and BEC groups evolve with major news events and macroeconomic trends, the cyclical nature of advanced email threats remains remarkable consistent.
With COVID-19 providing powerful leverage for this spring's wave of credentials harvesting campaigns, it's safe to assume cybercriminal organizations will soon be putting those logins to use in new ATO-based attacks.
Yet despite the threat, it's unclear how many organizations are deploying identity-based phishing defenses capable of blocking today's most advanced email threats—including those launched from compromised email accounts belonging to internal executives or outside suppliers.
Since 2016, these kinds of advanced email threats have led to an estimated $8.6 billion in business losses per year.
If the phishing and BEC scams orchestrated by groups like Ancient Tortoise and Cosmic Lynx are any indication of what's to come, the first half of 2020 offers plenty of insights for the challenging days ahead.
To learn more, download a complimentary copy of the H2 2020 Email Fraud and Identity Trends Report from Agari.