What is Vendor Email Compromise?
Anatomy of an Attack
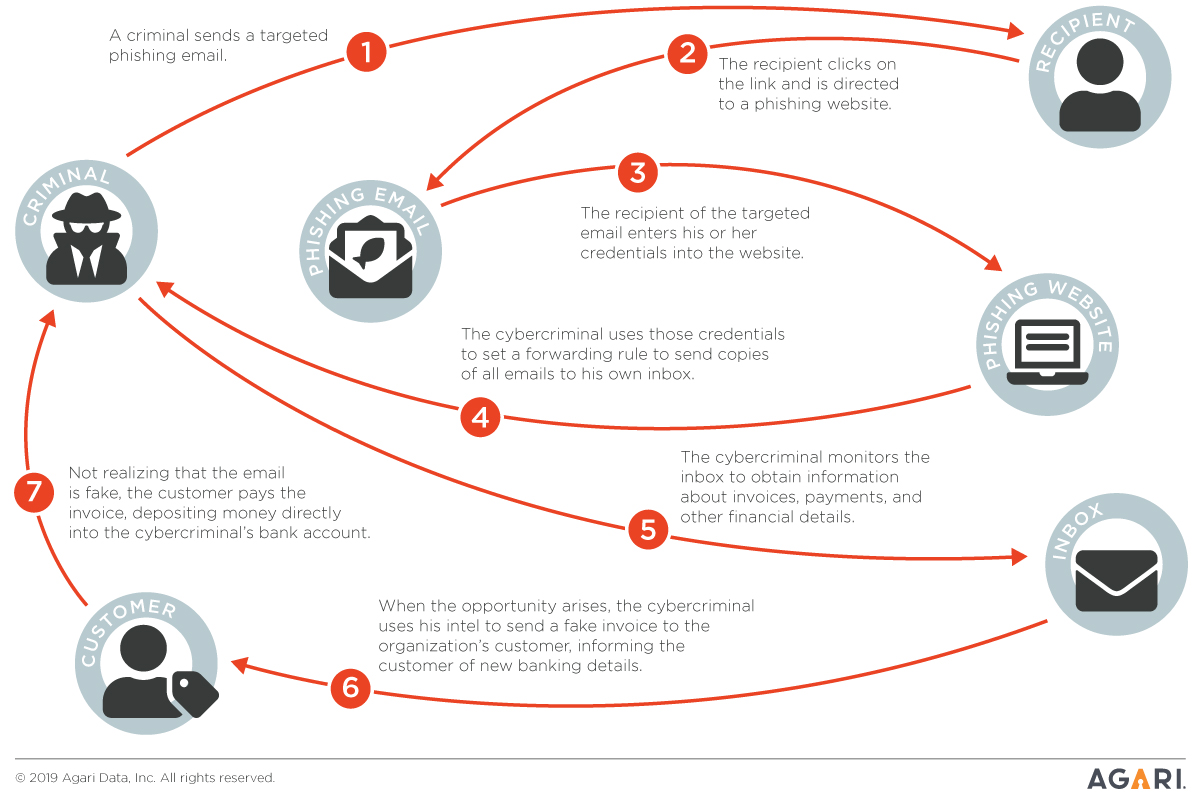
Vendor Email Compromise spreads from one business to others like a contagion across the extended enterprise. Well-funded, organized cyber crime rings use hijacked business email accounts and social engineering tactics to gather insider information that is then used to create meticulously crafted and timed attacks. In this way supply chain partners inherit risk from each other as employees are tricked into performing seemingly innocuous, but harmful actions.
PHASE 1: Initial Access
Compromise Email Account
The first step in the VEC attack chain is to compromise business email accounts that can be used to collect intelligence to exploit later in the attack process. Phishing messages often mimic Microsoft OneDrive or DocuSign login pages, as well as voicemail and fax notifications.
PHASE 2: Set Up
Lie in Wait
Once a business email account has been compromised, forwarding rules are set up to allow criminals to lurk undetected as they read emails and collect intelligence, waiting for the opportune moment to attack (e.g., when an invoice is due).
PHASE 3: Reconnaissance
Gather Intelligence
Equipped with a legitimate identity and insider information, criminals often target employees involved in the payment process and further gather key pieces of information such as AP aging reports containing invoice amounts, payment terms and billing contact details.
PHASE 4: Monetize
Defraud the Business
Bogus, but ultra-realistic emails are sent with near perfect timing and context tricking recipients into changing payment instructions, paying fake invoices, and disclosing sensitive information, defrauding the organization or individual.
The Agari Advantage
Detect Fake Email From Legitimate Accounts
VEC attacks originate from legitimate email accounts that have been hijacked. Messages pass domain authentication and sail right through whitelists and other security controls.
On visual inspection, even highly trained security experts can’t spot them, and they contain highly-convincing business and personal details.
Agari detects these rapidly evolving VEC attacks and can prevent them from reaching employee inboxes through policy-based, automated forensic analysis that understands the identity behind the message.
The Emergence of VEC
Agari researchers uncovered a West African cybercriminal organization that uses VEC to surveil the communications of hundreds of companies and steal millions from their global supply chains.
This guide offers a first-hand, in-depth look into how the VEC attack chain unfolds.
Email Account Takeover Protection
The first step in preventing a VEC attack is detecting compromised business email accounts.
Agari inspects incoming messages, but also messages flowing from employee-to-employee across the organization for indicators of compromise.
This unique approach can detect fraudulent messages originating from legitimate email accounts.
See Cloud Email Protection In Action
Try this product tour to see why companies use Cloud Email Protection to protect their inboxes.


